Services of Operating Systems

 |
| A View of Operating System Services |
An operating system provides an environment for the execution of programs.
It makes certain services available to
programs and to the users of those programs. The specific services provided, of
course, differ from one operating system to another, but we can identify common
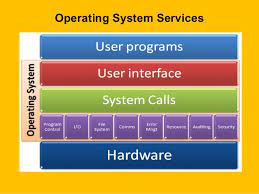
classes. Figure shows one view of
the various operating-system services and how they interrelate. Note
that these services also make the programming
task easier for the programmer. One set of
operating system services provides functions that are helpful to the user.
User interface
Almost all operating systems have a user interface (UI). This interface can take several forms. Most commonly, a graphical user interface (GUI) is used. Here, the interface is a window system with a mouse that serves as a pointing device to direct I/O, choose from
menus,
and make selections and a keyboard to enter
text. Mobile systems such as phones
and tablets provide a touch-screen
interface, enabling users to slide their fingers across the screen or press buttons on the
screen to select choices.
Another option is a command-line
interface (CLI), which uses text commands and a method for entering them (say, a keyboard for
typing in commands in a specific format with specific
options). Some systems provide
two or all three of these variations.
Program execution
The system must be able to load a
program into memory and to run that program. The program must be able to end
its execution, either normally or abnormally (indicating error).
I/O operations
A running program may require I/O,
which may involve a file or an
I/O device. For specific devices, special functions may be desired (such as reading from a network interface or writing to a file
system). For efficiency and protection, users
usually cannot control I/O devices directly.
Therefore, the operating system must provide a
means to do I/O.
File-system manipulation
The file system is of particular
interest. Obviously, programs need to read and write files and directories.
They also need to create
and delete them by name, search for a given file, and list file information.
Finally, some operating systems include permissions management to allow or deny access to files or directories based on file
ownership. Many operating
systems provide a variety of file systems, sometimes to allow personal
choice and sometimes to provide specific features or performance characteristics.
Communications
There are many circumstances in which one process needs to exchange information with another process. Such
communication may occur between processes that
are executing on the same computer or between
processes that are executing on different computer systems tied together by a network. Communications may be implemented
via shared
memory, in which two or more processes
read and write to a shared section of memory, or message passing, in which packets of information in predefined formats are moved between processes by the
operating system.
Error detection
The operating system needs to be detecting and correcting errors constantly. Errors may occur in the CPU and
memory hardware (such as a memory error or a power failure),
in I/O devices (such as a parity error on disk, a connection failure on a network, or lack of paper
in the printer),
and in the user program (such as an arithmetic overflow
or an attempt to access an illegal memory
location). For each type of error, the operating system should take the appropriate action to ensure correct
and consistent computing. Sometimes, it has no
choice but to halt the system. At other
times, it might terminate an error-causing process or
return an error code to a process for the
process to detect and possibly correct.
Another set of operating-system functions exists not
for helping the user but rather for ensuring the
efficient operation of the system itself. Systems with multiple processes can gain efficiency by sharing the
computer resources among the different
processes.
and in the user program (such as an arithmetic overflow
or an attempt to access an illegal memory
location). For each type of error, the operating system should take the appropriate action to ensure correct
and consistent computing. Sometimes, it has no
choice but to halt the system. At other
times, it might terminate an error-causing process or
return an error code to a process for the
process to detect and possibly correct.
Resource allocation
When there are multiple processes running at the same time, resources must be allocated to each of them. The operating system manages many different types of resources. Some (such as CPU cycles, main memory, and file storage) may have special allocation code.
Whereas others (such as I/O devices) may have much more general request and release code. For instance, in determining how best to use the CPU, operating systems have CPU-scheduling routines that take into account the speed of the CPU, the process that must be executed, the number of processing cores on the CPU, and other factors. There may also be routines to allocate printers, USB storage drives, and other peripheral devices.
Logging
We want to keep track of which programs use how much and what kinds of computer resources. This record keeping may be
used for accounting (so that users can be
billed) or simply for accumulating usage statistics.
Usage statistics may be a valuable tool for system administrators who wish to reconfigure the system to improve computing
services.
Protection and security
The owners of information stored in a multiuser or networked computer system may want to control use of that
information. When several separate processes execute concurrently, it should
not be possible for one process to interfere
with the others or with the operating system itself. Protection involves
ensuring that all access to system resources is
controlled. Security of the system from outsiders is also important. Such
security starts with requiring each user to authenticate him or herself to the system,
usually by means of a password, to gain access to system
resources. It extends to defending external I/O devices,
including network adapters, from invalid access attempts and recording all such connections for detection of break-ins. If a system is to be
protected and secure, precautions must be
instituted throughout it. A chain is only as strong
as its weakest link.

